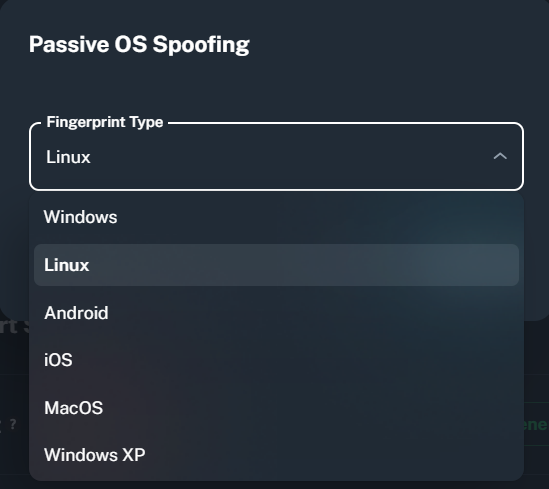
This feature is only available in the Proxidize Business plan.
What is Passive OS Fingerprinting?
Passive OS spoofing/fingerprinting is a technique used to determine a remote system's operating system (OS) without actively probing it. Instead of actively sending packets to the target system, passive OS fingerprinting relies on analyzing the characteristics of network traffic generated by the target system, such as TCP/IP stack behavior, packet size, and how packets are fragmented and reassembled.
In simple terms, this technique will allow you to spoof the OS used for all your requests when using the proxies if a different OS is selected rather than the original OS running on the machine.
By default, Linux is the OS used when running the proxies. It can be changed to Windows with a few clicks to spoof the OS, however you can change it to whatever OS you prefer by using the "Change" button next to the Passive OS Spoofing section.